Overview
Proxying search and recommendations through your server is usually a bad idea. It adds latency, complexity, and can be a security risk. Instead, Trieve allows you to create and manage API keys that can be used directly in the client. To create an API key, use the create Organization API key route.- TS-SDK method: createApiKey
- Python SDK method: create_api_key
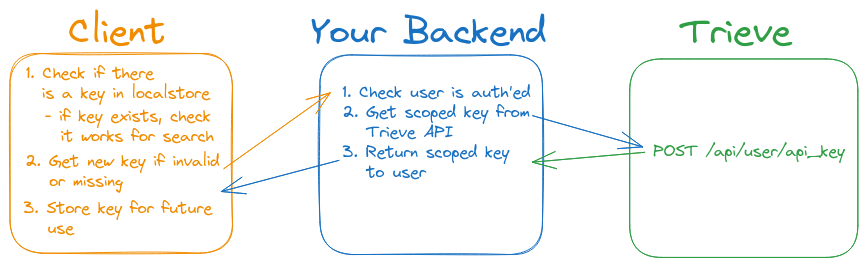 All of the below examples can be used in combination with each other. For example, you can create an API key that can only access specific organizations, datasets, and tags within those datasets.
All of the below examples can be used in combination with each other. For example, you can create an API key that can only access specific organizations, datasets, and tags within those datasets.
Limit to read-only access
Specify therole field with the value 0 in your request.
curl
Set a time expiry
Specify theexpires_at field with the time in the future that the API key should expire in your request. This field accepts only ISO 8601 formatted dates.
curl
Scope access to specific organizations
Specify theorganization_ids field with the organization IDs that the API key should have access to in your request.
curl
Scope access to specific datasets
Specify thedataset_ids field with the dataset IDs that the API key should have access to in your request.
curl
Scope access to specific routes
curl
Scope access to chunks matching a filter or other search request payload fields
Specify a filter in thedefault_params field in your request. This filter will be applied to all requests made with this API key.
You can use this to restrict access to data with more granularity than just dataset or organization.
curl